virus ေၾကာင့္ "Hidden" ျပန္ေဖာ္မရခဲ့ရင္
File ေတြကုိ သူမ်ားေတြ႔မွာစုိးလုိ႔ Hidden လုပ္ျပီးထားမယ္ အဲ့ဒီအခါစက္ထဲကုိ virus ၀င္လုိ႔ hidden file ေတြျပန္ေဖာ္မရခဲ့ရင္ လုပ္လုိ႔ရ တဲ့ နည္းေလးကေတာ့ Registry တြင္ျပန္လည္ ျပဳျပင္ေပးရပါတယ္ လုပ္နည္း ကေတာ့....
ပထမဦးဆုံး Run box ကုိေခၚ Run box ေခၚနည္းကေတာ့သိမယ္ထင္တယ္ (window key+R) ႏုိပ္လုိက္ပါ....
အဲ့ေဘာက္ထဲမွာ ဒီလုိရုိက္လုိက္...regedit...လုိ႔ရုိက္...ေပၚလာတဲ့ေဘာက္ထဲမွာ ဘယ္ဘက္အျခမ္းမွာ Hkey Local Machine ဆုိတဲ့ ေခၚစဥ္ကုိ ျဖည္လုိက္ပါ +ေလးကုိႏုိပ္ျပိးေတာ့ေပါ့ေနာ္...
အဲ့ေအာက္ကေနမွ Software ျပီးရင္ Microsoft ျပီးရင္ Windows ျပိးရင္ Current Version ျပီးရင္ Explorer ျပီးရင္ Advanced ျပီးရင္ Folder ျပီးရင္ Hidden ျပိးရင္ SHOWALL ကုိနုိပ္လုိက္ ညာဘက္ အျခမ္း က CheckedValue ကုိလစ္ႏွစ္ခ်က္ေခါက္...Value data ကုိ (1)ထားေပးပါ....စက္ကုိ Restart ခ်ေပးလုိက္ပါ....
HKLM\Software\Microsoft\Windows\Current Version\Explorer\Advanced\Folder\Hidden\SHOWALL-------CheckedValue မွာ Value data ကုိ 1 ထားပါ...။
Whatever the name of the virus was, it had the nasty habit of hiding objects and leaving behind harmful shortcuts that were seemingly for those hidden objects but actually executed or ran the virus itself when clicked.
An average user wouldn’t know any better, making it hard for them to view and recover important data.
Now that the situation is briefly described, it’s time to know the possible steps on how to show and/or unhide hidden files and folders. Let the invisible become visible!
Note: This guide is specifically made for Windows 7. However the procedure is possibly applicable to Windows XP and Vista with only a few differences lying here and there.
Furthermore, no additional software will be needed. Only the tools natively found on Windows will be used.
Lastly, during this guide I’ll be interchangeably using objects to refer to files and folders.
Folder Options
If files and folders are hidden, the initial step is enabling the showing of hidden files and folders in Folder options. To do this,
Fix Files and Folders Hidden by Virus
Being an advanced computer user, friends and colleagues would generally turn to me when problems on their computers arise. This one time a computer was infected by a virus. Obviously, the needed solution was to entirely remove the infection. But what was more important was reverting the damage it caused: The virus hid important files and folders.Whatever the name of the virus was, it had the nasty habit of hiding objects and leaving behind harmful shortcuts that were seemingly for those hidden objects but actually executed or ran the virus itself when clicked.
An average user wouldn’t know any better, making it hard for them to view and recover important data.
Now that the situation is briefly described, it’s time to know the possible steps on how to show and/or unhide hidden files and folders. Let the invisible become visible!
Note: This guide is specifically made for Windows 7. However the procedure is possibly applicable to Windows XP and Vista with only a few differences lying here and there.
Furthermore, no additional software will be needed. Only the tools natively found on Windows will be used.
Lastly, during this guide I’ll be interchangeably using objects to refer to files and folders.
Folder Options
If files and folders are hidden, the initial step is enabling the showing of hidden files and folders in Folder options. To do this,
- In the Control Panel, open Folder Options.
- Click the View tab.
- Under Advanced settings, click Show hidden files, folders, and drives, and then click OK.
This step was the first thing I did. But the virus I dealt with had more up its sleeves! The procedure above was not enough; The hidden files and folders were still not shown.
Protected Operating System Files
The virus managed to modify the attributes so as not only make the affected objects hidden, but also make them read-only (cannot be modified), and become system files. System files are specially hidden to prevent users from accidentally changing and/or deleting them (which might cause system instability and crashes). Call them super hidden if you want.
The step is still fairly simple and similar in order to view these system files.
- In the Control Panel, open Folder Options.
- Click the View tab.
- Under Advanced settings, uncheck Hide protected operating system files (Recommended).
From Hidden to an Ordinarily Visible Files
The previous steps were needed in order to just view the hidden files and folders. To make them permanently visible again, we need to remove the hidden, read-only, and system file attributes or properties. The common way to do this is to
- Right-click the file or folder, and then click Properties.
- Next to Attributes, uncheck Hidden and/or Read-only check box(es), and then click OK.
There are cases however when the check boxes are grayed out which means they cannot be changed. A more advanced method is by using the Command Prompt and use the attrib command.
Attrib CMD Command
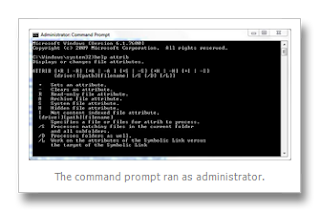
- Click the Start button. In the search box, type cmd and then press Enter.
- In the command prompt, type
attrib [drive]:[path][filename] -s -h -r /s /dFor example, foobar.doc in the folder location C:\Documents\Sample has been modified by the virus to make it a hidden system file. To revert this I’ll simply type in the command prompt:
The [drive] is the hard disk drive letter, while [path] is the address/path/location of the target file(s), and [filename] is the name of the target file(s).
The -s -h -r removes the system file, hidden, and read-only file attributes respectively.
The /s seeks files in the current folder and all its subfolders that matches the [filename] input.
Finally /d will mean folders are processed as well for attribute modification.
attrib C:\Documents\Sample\foobar.doc -s -h -r /s /dIf you happen to know that everything in a folder aren’t hidden system files and/or folders, you can use *.* instead of specifying a [filename].
attrib [drive]:[path]\*.* -s -h -r /s /dSo, for instance, if a removable flash drive is infected and all its objects are gone, simply type in the command prompt:
attrib [drive]:\*.* -s -h -r /s /dDepending on the current user access, the attrib may not work properly. It is therefore recommended to run the command prompt as an administrator.
Final Thoughts
With the last step above, I was able to recover the lost files. I then deleted the malicious shortcuts and got rid of the virus altogether. Problem solved.
One final piece of advice: install a reliable anti-virus program! :)







